Security Risks From Printers - Know Your Risk
Imagine credit card numbers for all of your customers and how valuable they are to your business. Now think about how valuable they would be if they...

Most IT departments do not commonly address the topic of printer security, but it should be. Printer security protects your business from hackers and helps prevent costly data breaches. Most IT professionals and small businesses don't think about printer security until they've been breached, but it's important to protect yourself by taking simple steps now. Here are some tips for how to protect your business and its data.
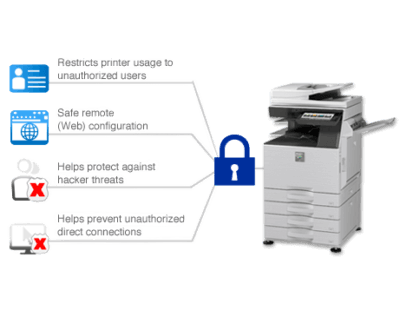
Protecting your company's data is crucial for business executives and owners. Printer security is one way to ensure that your printers and copiers are safe from hackers, malware and unauthorized access. Take these steps to keep your printer secure:
Printer security is not a top priority for many IT departments. Cybersecurity plans generally focus on network security, computers, servers and other endpoints. When discussing printers, there is plenty of discussion on the latest features, but security isn't usually high on the list--and it should be.
Many examples of printer security breaches have occurred in businesses worldwide. Some of these include:
The security of your data is paramount, and it's important to understand the risks associated with printers, MFPs and other office equipment. Data breaches can happen through printers and copiers in several ways. Below are the two most often-seen scenarios.
Now that the methods and risks of a data breach from your printer or copier have been outlined, how can your business protect itself from falling victim? Below, we outline several ways to stay safe.
Encryption is the only way to protect data in transit from device to device. Encryption also protects data at rest. For example, if you encrypt the hard drive on your computer and then lose it or have it stolen, anyone who finds the device will be unable to access any of your files unless they have the decryption key.
Encryption is also required for medical organizations such as hospitals and clinics; financial institutions like banks, credit unions and investment firms; government agencies (including law enforcement) that handle sensitive information such as social security numbers or medical records; as well as any business that handles customer credit card numbers or other personal data like addresses or phone numbers.
Unpatched operating systems, firmware, applications and software are common causes of data breaches. While it's essential to ensure that your printers are patched, it's also crucial to have them installed on a secure operating system.
If you're running Windows Server 2003 or earlier versions of Windows Server, you should upgrade to one of the current versions as soon as possible (Windows Server 2019 is currently available). If you can't upgrade right now, then use Microsoft EMET (Enhanced Mitigation Experience Toolkit) to help protect against attacks while you wait for updates from Microsoft.
Authentication protocols like LDAP can be used to limit access to printers. If you're using an authentication protocol, it is important that you set up appropriate authorization controls so that only authorized users can print to particular printers. You can also use ACLs (Access Control Lists) to control who has permission to print jobs on the printer(s).
Data breaches can devastate businesses, but they can be prevented with printer security.
Data breaches are becoming more and more common, but there are several things you can do to protect your business from them. Here are three simple steps to take:
Printer security is one of the many ways to protect your business from data breaches. A good place to start is by contacting your print partner for more information about their security solutions and how they can help protect against data breaches. We've got you covered if you need assistance finding the right printer solution! Our experts are here to help with everything from picking out new printers and MFPs to deployment planning and implementation assistance. Schedule a free print security assessment today!

Imagine credit card numbers for all of your customers and how valuable they are to your business. Now think about how valuable they would be if they...
Introduction In today's digitally connected world, ensuring the security of your company's IT infrastructure is a top priority. However, many...
When talking about security, most people understand the need for antivirus software and VPNs to protect computers and networks from potential...